In-brief: connected medical devices pose a number of risks to patients, including the threat of “targeted killings,” according to a report by Intel Security. The fix: better application design and more public-private sector cooperation.
Connected health devices are poised to revolutionize the way healthcare is provided and could dramatically reduce the cost of caring for the sick within the space of a generation. But these new devices also introduce new threats, including the possibility of “targeted killings” by way of implanted or wearable medical devices, according to a report from the firm Intel Security.
Connected health products will demand an increased focus from medical devices makers on information security. They also demand a new approach to the regulatory approval process by the federal government if the promise of connected health technologies is to be realized. That’s the conclusion of a new report out from Intel Security and The Atlantic Council. The report: The Healthcare Internet of Things: Rewards and Risks, which assesses the security risks of connected health technologies.

The report notes research from GE that estimates new technology could shave $63 billion from healthcare costs in just the next 15 years. Much of that would come from reduced costs for hospital equipment. But those savings come at a cost, according to the report’s authors. Specifically: the threat of “accidental failures” that erode patient (and public) trust. Patient privacy and the need to protect sensitive health data is another immediate concern, as recent compromises at Athena Health and, last week, Premera Blue Cross illustrate.
[Read more Security Ledger coverage of security issues affecting connected health devices. ]
Intentional disruption of entire classes of networked medical devices by motivated attackers like hacktivists, spies or terrorist groups is a concern for patients wearing connected health devices that are critical to their safety. The group also considers the threat of “targeted killings” by way of the disruption of- or malicious attacks on connected medical devices to be a possible – though remote – concern. However, threats like the sophisticated Stuxnet malware used to disable Iran’s uranium enrichment operation are proof that even super-sophisticated, low-probability attacks are possible, given a motivated attacker, the authors note.
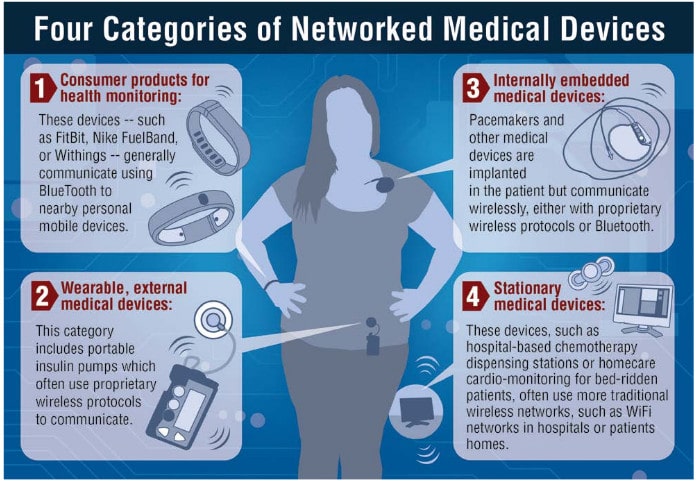
The report identifies a number of risks that run throughout the medical device sector. Among them:
- The lack of a standard operating environment, architecture or protocols for medical devices. “Where mobile phones or tablets operate on a relatively small set of standard technologies (Android or Apple, WiFi only or WiFi and 3G or 4G), medical devicemanufacturers tend to assemble a grab-bag of technologies, depending on the size of the device,” the authors observe.
- The lack of standard programming language across the medical device industry. This leads to disparities between medical devices and applications. Often, device makers hue to older hardware and software components and languages in order to simplify the maintenance of FDA-approved products and code.
- The absence of rigorous access control and credential-management features. As security researchers have been quick to note: medical device makers are fond of using embedded (hard coded) credentials to provide emergency access to their devices. Such techniques pose considerable risks to patients. However, medical device makers must strike a balance between security and usability.
- The lack of flexible maintenance and update features. While device makers have been quick to implement new, connected features in their products, features that allow them to update the software running those products has lagged. Lingering concerns about the impact of software updates on FDA approval for the device are largely unfounded, but may contribute to a reluctance to embrace transparent, “OTA” (over the air) update features that are common in other Internet connected platforms and products.
The report calls for a number of changes. At the top of the list: a move by medical device manufacturers to embrace “secure-by-design” principles for research and development. “Adding security features to products after their initial rollout is a losing battle. It is simply too costly and ineffective to try to secure systems already in the possession of the end user,” the report concludes. In a report by the Food and Drug Administration (FDA) in October, the U.S. government also called for “secure by design” principles to be used in the creation of new, connected health products.
Closer cooperation with security experts, including the use of bug bounties to encourage researchers to look at medical devices are recommended.
The report shies away from calling for stricter regulation of connected health devices. Rather, it calls for closer cooperation between regulators and private firms, and changes at the federal level that make it easier to get new, connected health products evaluated and approved by government regulators. Removing barriers to retiring legacy hardware and application software will likely lead to rapid improvement in the security features and capabilities of connected medical devices and other health products, the authors conclude.

Good post. I learn something totally new and challenging on websites I stumbleupon everyday.
It’s always exciting to read through articles from other authors and use a little
something from other web sites.
Hello I am so grateful I found your website,
I really found you by error, while I was browsing on Digg for something else,
Nonetheless I am here now and would just like to say many thanks for a fantastic post and a all round exciting blog (I also love the theme/design),
I don’t have time to browse it all at the moment but I have saved it and also added in your RSS feeds, so when I have time I will be back to read a lot more, Please do keep up
the fantastic work.
I do not understand this desire to connect medical devices to the internet.
Shouldn’t we be trying to find a way to provide health solutions to people
that are not predicated on anything like “the internet of things”? or Networks?
In the meanwhile, as security researchers we must also be aware that these
sorts of medical devices can be weaponised (as the recent expose on the US
looking into using bin Laden’s medical issues and possible medical implants
to et to him – like it would only be used once, or it could ever be
used ethically!).
Shouldn’t we be baking morality into our technology by not making it some-
thing which can be hacked (especially remotely) that doesn’t require “less
bugs” – which is to say, why is this even included in the rubric of the
“Internet of Things” to begin with? Refrigerators – MAYBE… but must we
pump this sort of connectivity into everything?
Even the show Homeland, fictional as it was, evidenced just how treacher-
ously such technologies can be used – and why should they be used at all
if there are safer solutions?
In the meanwhile you create a cost-to-bug-finding ratio that will encourage
only certain sorts of actors to address the problem. Splashing out on a bunch
of medical equipment may itself cause a lacuna where those with interest cannot
afford the devices but have ideas on how to exploit them. That doesn’t work out
well. Look at the situation with Chris Roberts as evidence that people want to
play with things… and see if they can break them.
If only companies with contracts and big research budgets can tackle this legit-
imately then what will people do to be able to play that cannot afford to do so?
The typical broke researcher what… steals? All due respect but most freelancers
who do not want to sell out barely find ways to afford Burp Pro or a real copy of
IDA. Can one do without them? Sure, but like airplanes and medical devices the more
you try to do with less, the worse off the independent researcher can be. One can’t
exactly pirate an insulin pump. One probably can’t even pirate Coverity of any of
Immunity’s products with a pricetag.
Not everybody wants to work for Mandiant.
The industry needs to realise we are a gluttonous industry. IoT will make us moreso.
In the meanwhile thousands of people want to make a name for themselves.
How can it end well if we can’t even stop the networking of medical devices?
That should’ve read, ‘Coverity, or any of Immunity’s “products-with-a-pricetag”‘.
Hi there, after reading this awesome paragraph i am also delighted to share my
familiarity here with colleagues.
Magnificent website. A lot of useful info here. I am sending it to a few friends ans also sharing in delicious.
And certainly, thanks to your effort!